Legacy security based on a network perimeter, or a castle and moat approach, is no longer fit for purpose. Mobile Mentor outlines how a zero trust architecture can be deployed using Microsoft 365 E3 licences in this second article in the Zero Trust series.
Companies are hiring and onboarding new employees remotely, often working on personal devices and using cloud applications, so the traditional network perimeter is long gone.
We used to feel we could trust our VPN and our passwords. Now that trust has been broken and our VPNs and passwords are often the weakest link. We have entered an era of zero trust.
Zero Trust means “guilty until proven innocent.” Every request to access company information is assumed to be a security breach. Each request gets explicitly verified and only the requested resource is provided. Revisit our first article in the Zero Trust series to get a refresher on the three principles.
If the request is indeed a breach, and the attacker gets a foothold in your environment, zero trust limits the blast radius by preventing lateral movement using least privileged access and just-in-time access.
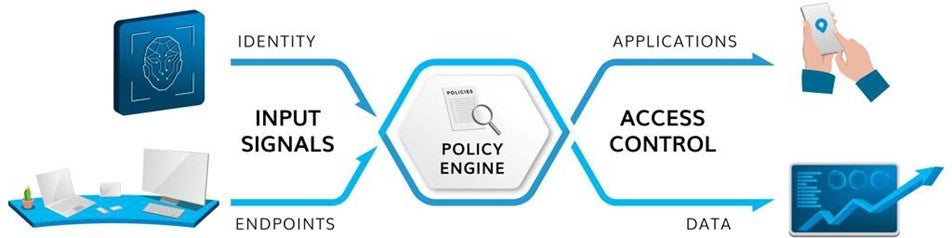
Deployment blueprint with Microsoft 365 E3
Zero Trust can be deployed effectively and at scale using standard Microsoft 365 E3 licenses. The following outlines practical guidance for the three parts of the Zero Trust architecture.
Input Signals
Cloud Identity: Configure modern cloud identity with Azure Active Directory, biometrics, self-service password reset, multi-factor authentication, and single sign-on, if possible. Decommission on-premise AD when possible and retire any tools that complicate your identity infrastructure.
Corporate Devices: Enroll all company-owned devices, including laptops and smartphones, in Microsoft Endpoint Manager/Intune. Legacy devices in SCCM can be co-managed in Intune, or Hybrid Azure AD Joined (HAADJ). Ultimately you will want to migrate to Azure AD joined and fully managed in Intune.
Personal Devices: Protect Office 365 data on BYO and unmanaged smartphones via Intune App Protection Policies. Assure your employees that their personal privacy is respected while company data is protected. Use Azure Virtual Desktop or Windows 365 for BYO MacBooks, and Windows.
Endpoint Protection: Configure Defender for Endpoints with anti-malware, web filtering and endpoint firewall to identify and block endpoint breaches. Set-up rules to force the device back into a trustworthy state when it is compromised.
Device Encryption: Avoid regulatory notifications for minor security incidents and reduce your insurance premiums by insisting on encryption for all devices. This may require replacing old Windows devices that don’t have a TPM 2 chip.
Policy Engine
Conditional Access: Configure risk-based Conditional Access policies in ‘report mode’ initially. Then apply a gentle set of restrictions to high-risk situations and gradually tighten the policies as confidence and experience allows.
Change Management: Employee push-back is inevitable as policies restrict certain activities that were previously permitted. Ultimately the user experience will be much better, but it will be different and that requires a change management approach. Regular communication to execs and end-users is critical to ensure the success of the Zero Trust journey.
Education: Ensure your people are not the weakest link by providing a steady stream of security awareness education and communications on good security practices.
Access Control
Risk Mitigation: Configure Defender for Office 365 to protect against malicious links, phishing attacks, attachments, and websites. Configure Defender for Identity to limit lateral movement and account compromises in the event of a breach.
Azure App Proxy and Private Link: Eliminate the need for a VPN by using a secure connection to legacy applications and on-premise web apps with the Azure AD App Proxy. For companies with substantial on-premise infrastructure, enable Azure Private Link to extend Zero Trust capabilities from the cloud to on-premise. Azure Private Link can be skipped by going all-in with modern cloud applications.
Information Protection: Implement Information Protection by defining sensitive data categories and manually applying labels. Assign policies to labels to trigger protective actions, such as encryption or limiting access to third-party apps.
Better security plus better employee experience
The elegance of Zero Trust is that it improves endpoint security AND employee experience. This is very different to traditional security models where more security meant more restrictions.
Proactive IT leaders now have an opportunity to measure specific metrics before and after the deployment of Zero Trust to demonstrate the improvements in security and experience.
This visibility is important to stakeholders who invested in E3 and want to see a return on investment before committing to invest in E5 in the future.
Why upgrade to E5?
You can go a long way towards deploying Zero Trust with E3. At some point, however, you will want to upgrade to E5. Yes, E5 comes with a higher price tag, but the uplift from E3 to E5 is a small price to pay compared to the $9 Million cost of an average cyber security breach.
In part 3 of our Zero Trust series, Mobile Mentor will explain how E5 enhances a Zero Trust architecture at enterprise scale.
Get your regular fix of thought leadership from Mobile Mentor by joining their newsletter.
Read the rest of the Zero Trust series to round out your knowledge:
Part 1: Underlying principles of Zero Trust
Part 3: Zero Trust – At Scale
Part 4: 6 transformations to disrupt your legacy IT operations

Mobile Mentor is Microsoft’s 2021 Partner of the Year for endpoint ecosystems. Certified by Microsoft, Apple and Google, they work tirelessly with clients to balance endpoint security with an empowering employee experience.