At Pax8, we take cybersecurity seriously. This is why we recommend our managed service provider (MSP) partners implement the CIS Security Controls, a global framework with broad, yet simplified best practices for cybersecurity. But while the basics laid out by the CIS Controls offer plenty to chew on for MSPs looking to bolster their clients’ cybersecurity, putting each of the 18 Controls and their safeguards into place is much easier said than done.
What we discovered in our research was that there wasn’t a single source of truth out there that explored each of the CIS Controls and how to effectively evaluate each of their components. We knew that for our partners to take full advantage of this framework, they needed to understand its nuance, context, and definitions clearly. That’s why we worked with our partners and CIS directly to develop the “CIS Controls Handbook: A Visual Guide to Evaluating Cybersecurity.” This comprehensive, proprietary resource offers visualizations for each Control and sub-Control so MSPs know the ins and outs of each and how they can begin to plan for implementation. Read on to learn how we made this mammoth endeavor happen.
Bringing together the MSP community
We started by engaging the Center for Internet Security® (CIS) itself. CIS is a global, community-driven nonprofit that works with individuals in the IT and cybersecurity industry to develop benchmarks for preventing and mitigating cyber threats.
With this foundation in place, we sought and received input from more than 30 contributors spanning from IT professionals implementing cybersecurity measures to developers creating the products needed. With the help of our partners, we were able to learn more from those on the ground — what they did, what worked, and what their best practices were when it came to implementing CIS Controls.
Our purpose
The purpose behind creating this visual handbook was to develop the go-to guide to assist security professionals in navigating how to align their cybersecurity stack with the CIS Critical Controls and Safeguards. To design this clear and actionable guide, we worked with our collaborators to create visual representations of each safeguard’s language broken down into specific taxonomical elements. Because this framework is dense, developing a visual tool ensures a digestible way for MSPs to understand how the 153 safeguards that make up the CIS Controls interconnect.
Furthermore, these visual mappings offer security teams an effective way to evaluate their understanding of the breadth and depth of each safeguard, identify knowledge and coverage gaps, and plan accordingly. While software vendors may find the guide useful to align their products and service features with the CIS Controls, our primary focus is supporting security teams in strengthening their preventative security measures.
Behind the methodology
The handbook was born from an initiative to use the Controls’ taxonomical elements to create a questionnaire that classified each vendor’s products and services into the safeguards they serve. This involved creating a detailed evaluation criterion, including technical components and vendor attestation methods, to ensure that each solution provided comprehensive coverage for its corresponding safeguard. The result? We were able to classify and sort solutions that help MSPs and the organizations they serve meet each of the CIS Controls. Many of these solutions are available to provision in the Pax8 Marketplace.
How to use this document
This visual guide is not meant to replace the CIS Control guidelines; rather, it’s meant to bolster the great work CIS is already doing. It’s helpful to first get acquainted with the CIS Controls, CIS Implementation Groups, CIS Benchmarks, and the broader CIS body of work. The guide also assumes a baseline knowledge of security principles. If you don’t feel you have a solid grounding in this framework, our courses in Pax8 Academy can get you up to speed.
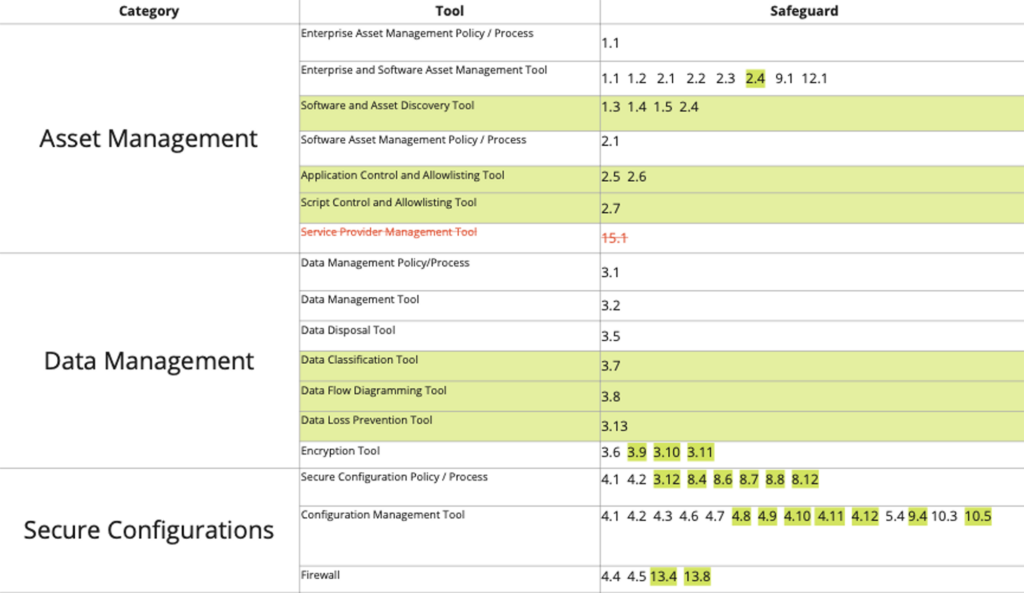
For an idea of how each of the Controls is mapped out, view the chart below:
Also, you can watch our video walkthrough to get started.
How Pax8 is implementing this work into the Pax8 Marketplace
The substantial work we have done with the community around this project doesn’t stop at a handbook. We’ve taken the knowledge gleaned from our research and built it right back into the Pax8 Marketplace.
Now, our partners have access to a new feature called Opportunity Explorer.
What is Opportunity Explorer?
Unveiled at this year’s Pax8 Beyond, this feature leverages data to pinpoint and answer customer needs, offering actionable data insights for partners to provide tailored recommendations and identify sales opportunities. Opportunity Explorer was designed with the power of machine learning and data-driven insights and was built on the wisdom of our 35,000+ partners to help MSPs identify gaps in coverage and capitalize on sales opportunities. Partners can search, filter, and sort opportunities in a completely reimagined user interface.
Here’s just some of what this feature can do:
- Highlight seat and product gaps
- Identify coverage vulnerabilities
- Search, sort, and filter based on customers’ needs
- Discover upsell/cross-sell opportunities
- Recommend actionable, data-driven insights
- Illuminate untapped revenue streams
How does Opportunity Explorer help partners and their clients strengthen their security postures?
Here’s what’s so great about Opportunity Explorer: It’s not just a way to earn more revenue from your clients; it’s a way to serve them better, with tailored security recommendations. Using best-in-industry security packages and CIS version 8, Opportunity Explorer shows you which of your customers may have security gaps and where, so you can engage those clients in a discussion around security.
Getting started with our CIS Controls Handbook and Opportunity Explorer
Together, our new handbook and the improvements we’ve made to the Pax8 Marketplace help you better serve your clients with improved cybersecurity measures while generating new revenue opportunities for your business. Log into the Pax8 Marketplace to give Opportunity Explorer a spin and download our CIS Controls handbook to tap into the collective knowledge of our partners and create a successful cybersecurity strategy for your clients.
Thanks to all the contributors to “CIS Controls Handbook: A Visual Guide to Evaluating Cybersecurity”
This publication is a result of a collaborative effort between Pax8, CIS, and a diverse group of industry leaders that span from practitioners to developers. Special thanks to our facilitators at the MSPs Global Data Systems and Blue Helm Technology.
Matt Lee, Senior Director of Security and Compliance, Pax8
Veronika Dombayeva, Vendor Strategy Analyst, Pax8
Charity Otwell, Director, Critical Security Controls, Center for Internet Security
Joshua Franklin, Senior Cybersecurity Engineer, Center for Internet Security
Bob Miller, Global Data Systems
Stephen Kellogg, Blue Helm Technology
Brandon Martinez, ZenTop Consulting
Dan Brinkmann, Summit Technology, LLC
Dawn R. Sizer, 3rd Element Consulting
Maria Scarmardo, Praxis Data Security
Henry Timm, Phantom Technology Solutions
Karen Stanford, Archstone Security
Kenneth Brothers, Information Security Risk Management
Marc P. Menzies, Overview Technology Solutions
Martin Perkins, Ki Security and Compliance Group