As a managed service provider (MSP), cybersecurity is perhaps the most important aspect you can help your clients navigate. This is why we advise implementing the Center for Internet Security’s (CIS) Critical Security Controls, a comprehensive global framework featuring straightforward best practices for cybersecurity. This framework also addresses the security standards used in the Asia-Pacific (APAC) region. In this blog, we’ll cover what the CIS Controls are, how they correspond to security standards specific to the APAC region, and how Pax8 can help our partners around the globe implement the security measures involved.
The importance of cybersecurity
Cybersecurity can be particularly challenging for organisations in APAC countries. In fact, more than half (59%) of organisations in this region have experienced a cyber incident, with 32% of these organisations suffering multiple incidents. Malware, phishing and password attacks together account for more than half of these incidents.
Cyberattacks are proving to be increasingly costly for APAC organisations — and that’s only getting worse. The average annual cost of cybercrime in the APAC region is expected to increase dramatically, from $8.4 trillion in 2022 to more than $23 trillion by 2027.
For MSPs operating in the APAC region, this not only presents a big challenge, as organisations will look to you for guidance on this growing problem; it also presents a big growth opportunity.
What are the CIS Controls?
The CIS Critical Security Controls consist of 18 Controls that together make up a framework for organisations looking to maximize their security, ranging from malware defense to incident management. These controls are also broken down into 153 safeguards that go into more detail about each of the Controls.
Pax8 advocates for adhering to the CIS Controls because they constitute one of the most comprehensive and robust cybersecurity frameworks available. The CIS Controls offer extensive coverage across all critical areas of cybersecurity, ensuring a thorough and effective approach to protecting systems and data. This framework also adheres to global security standards, including those specific to the APAC region and various industry requirements, which enhances its relevance and applicability across diverse environments.
While the fundamental principles outlined by the CIS Controls provide substantial guidance for MSPs aiming to enhance their clients’ cybersecurity, implementing each Control and its safeguards can be challenging. To assist with this, Pax8 collaborated with the Center for Internet Security® (CIS) and more than 30 contributors from the global MSP community to create a first-of-its-kind guidebook called CIS Controls Handbook: A Visual Guide to Evaluating Cybersecurity. This resource details each of the CIS Controls and offers a thorough evaluation of their components.
To see how each of the Controls is mapped out, view the chart below:
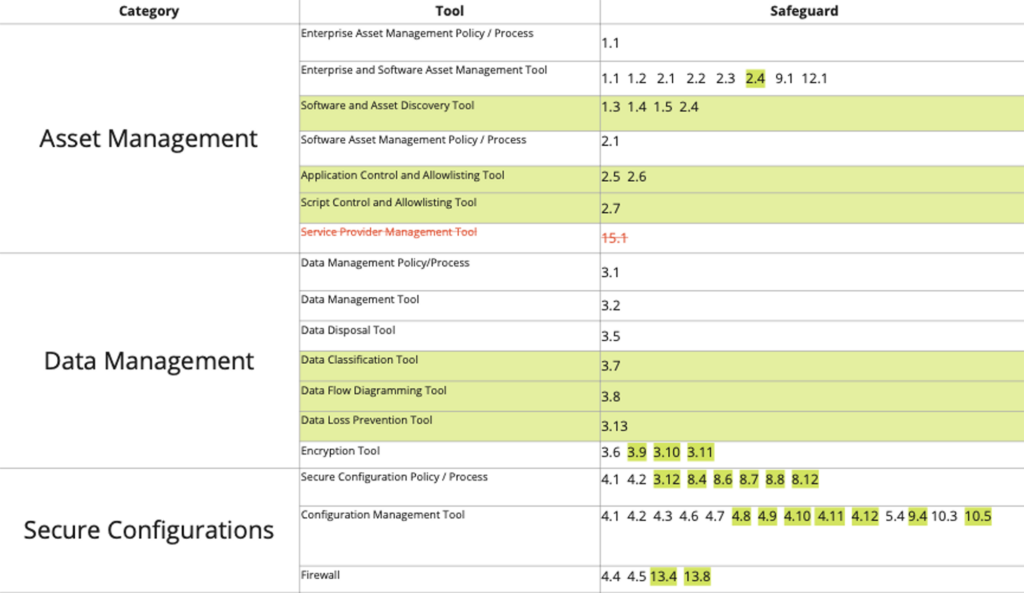
In addition, you can watch our video walkthrough to learn more.
What are the security standards local to the APAC region?
Adopting CIS Controls enhances the security protocols you or your clients may already be acquainted with in APAC, to help ensure compliance with both regional and industry-specific standards that are essential for operational integrity. Listed below are prime examples of commonly known security frameworks in APAC that align with the CIS Controls. These local frameworks share common goals with CIS Controls in establishing robust security practices.
ISO/IEC 27001
ISO/IEC 27001 is the globally recognized standard for information security management systems (ISMS). It outlines the necessary requirements for an effective ISMS and offers guidance for companies of all sizes and industries on establishing, implementing, maintaining and continually improving their ISMS. Essentially, it helps organisations become risk-aware and proactively identify and address weaknesses.
This standard will benefit your organisation because it can:
- Provide a centrally managed framework that secures all information in one place
- Prepare people, processes and technology throughout your organisation to face technology-based risks and other threats
- Secure information in all forms, including paper-based, cloud-based and digital data
- Save money by increasing efficiency and reducing expenses for ineffective defense technology
An example of where CIS Controls and ISO/IEC 27001 align: CIS Control 2 (Establish and Maintain a Software Inventory) maps to ISO 27001 Control A5.9 (Inventory of Information and Other Associated Assets).
The Essential Eight
The Essential Eight is a set of prioritized cybersecurity mitigation strategies developed by the Australian Signals Directorate (ASD) to help organisation protect against cyber threats. The eight measures it includes are: patching applications, patching operating systems, implementing multi-factor authentication, restricting administrative privileges, using application control, restricting Microsoft Office macros, user application hardening and doing regular backups.
These strategies can benefit your organisation because they can:
- Enhance cybersecurity posture: Reduces the risk of cyber threats through eight key mitigation strategies.
- Improve operational resilience: Ensures quick recovery from cyber incidents, maintaining business continuity.
- Facilitate compliance and trust: Helps meet regulatory requirements and builds trust with stakeholders by demonstrating commitment to cybersecurity.
An example of where CIS Controls and The Essential Eight align: CIS Control 6.4 (Require MFA for Remote Network Access) maps to “Multi-factor Authentication.”
SMB 1001
Also focused in Australia, the SMB 1001 is a multi-tiered cybersecurity standard designed specifically for small- and medium-sized businesses (SMBs). It provides a scalable approach to cybersecurity, starting with basic controls and advancing to more comprehensive measures, akin to the “colored belts” before the “black belt” of ISO/IEC 27001. The standard covers areas such as technology management, access management, backup and recovery, policies and procedures, and education and training.
This standard will benefit your organisation because it can:
- Be cost-effective compliance: SMB1001 offers a tiered approach, making it affordable for small and medium businesses.
- Build a strong foundation: Establishes essential security controls before tackling more complex standards.
- Simplify processes: Provides guides, evidence requirements, and automated action plans for easy compliance.
- Manage risk effectively: Real-time insights and risk treatment plans enhance cybersecurity risk management.
An example of where CIS Controls and SMB 1001 align: Within CIS Control 10 (Malware Defenses) many of the safeguards map to all tiers of Requirement 3 (Install anti-virus software on all organisational devices).
Singapore Cybersafe
The Singapore Cyber Safe Programme helps organisations in Singapore enhance their cybersecurity posture. It offers tailored guidance and certification schemes like the Cyber Essentials mark, which is aimed at SMBs. The programme focuses on implementing good cyber hygiene practices across categories such as assets (people, devices and data), secure/protect (virus/malware protection, access control and secure configuration), software updates, data backup and incident response.
This programme can benefit your organisation because it can:
- Enhance cybersecurity posture: Provides tailored guidance and certification schemes to improve cyber hygiene.
- Offer certification for SMBs: Offers the Cyber Essentials Mark for demonstrating adherence to good practices.
- Provide comprehensive protection: Covers key areas like virus protection, access control, and secure configuration.
- Instill incident preparedness: Focuses on software updates, data backup, and effective incident response.
An example of where CIS Controls and the Singapore CSA Cyber Essentials Mark align: CIS Control 17 (Incident Response Management) maps to the individual “Incident Response” measure.
How Pax8 can help
Work with your clients to determine which guidelines they must follow. Once you have their guidelines in order, you can use the Pax8 CIS Controls handbook to find where they correspond to the CIS Controls.
Then, log into the new Pax8 Marketplace, where you can use Opportunity Explorer to find solutions that fit those specific Controls. This new feature is designed to help you find solutions that are specific to your clients’ needs and has the CIS Controls built directly into the experience.
We are happy to share our learnings to help you create a successful cybersecurity strategy and grow your business with Pax8.
Not a partner yet? Learn about becoming a Pax8 partner here.





